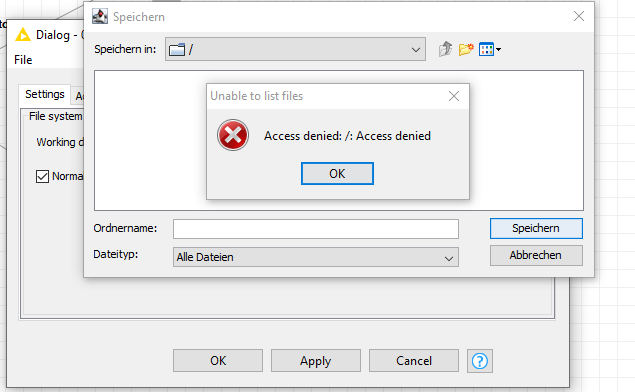
Hi when I try to connect to azure blob storage I get the repeated error "access denied
I am the owner of the storage account
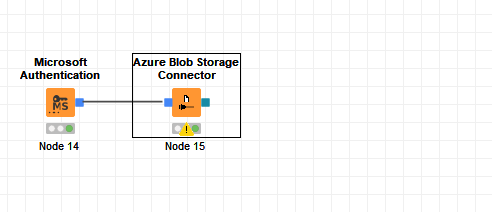
authentication seems to work properly in KNIME
Any ideas? Thanks a lot
Hi when I try to connect to azure blob storage I get the repeated error "access denied

I am the owner of the storage account
authentication seems to work properly in KNIME

Any ideas? Thanks a lot
Hey @Daniel_Weikert,
What I’d recommend is to run Azure CLI commands to attempt to access content in that Blog Storage container using the same authentication method to help determine if it’s an issue with configuration in KNIME or an issue with your IAM settings.
Regarding the configuration of the Microsoft Authentication node, what is the Authentication Mode set to? And is “Azure Blog Storage” selected under the “Request access to” section?
Cheers,
Hi sjporter,
thanks for your response.
Yes the access section should be set correctly
Access with Azure Storage Explorer works fine but I am not sure whether this equals access via cli commands considering access rights?
Hey @Daniel_Weikert,
Here’s more details on how to connect…
To authenticate via OAuth to Azure Blob Storage, the following things need to be in place:
Step 1: OAuth permissions (technically these are called “scopes”)
First, consent must be given to our registered Azure AD App (“KNIME Analytics Platform”) to access the Azure storage account on behalf of a user.
Consent can be given to our Azure AD App
log into your Microsoft account (if not already logged in)
consent to the access requested by “KNIME Analytics Platform” (this will only be prompted the first time)
In the Azure AD configuration under “Enterprise Applications” an Azure AD admin can grant access to the “KNIME Analytics Platform” app.
The globally unique Application ID of our Azure AD App is “cf47ff49-7da6-4603-b339-f4475176432b”, which can be useful for the admin to ensure that he is giving consent to the correct App.
Specifically, our Azure AD App must be given the delegated (!) permission “user_impersonation” for the Azure Storage service.
See here: Authorize with Azure Active Directory (REST API) - Azure Storage | Microsoft Docs
Step 2: The user herself must have permission to access a Azure Storage Account. This requires an admin to do the following:
In the Azure portal go to the Storage accounts
Click on the respective Storage Account
Click on “Access Control (IAM)”
Click on “Role Assignments”
Click “Add” > “Add role assignment”
Select role and the user (or a group it is in)
Click Save
It looks like you might’ve already completed step 1, but it might be worth trying to log in again with a fresh connection. Also, I would still recommend trying to authenticate via the CLI - it might lead to some insight into the root cause of the problem.
Cheers,
Thanks for the update.
I managed to sign in via access key. What I do not understand is why interactive authentication does not work as I am the owner. But the container access remains denied.
But this is me not understanding the azure security settings and no KNIME topic.
Thanks
This topic was automatically closed 7 days after the last reply. New replies are no longer allowed.