Hi,
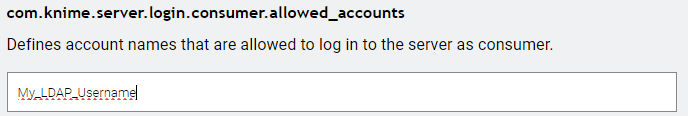
in principle, we have LDAP running with our KNIME Server. I can logon with my LDAP user name, e.g. as a consumer, when I explicitly add that user name to com.knime.server.login.consumer.allowed_accounts:
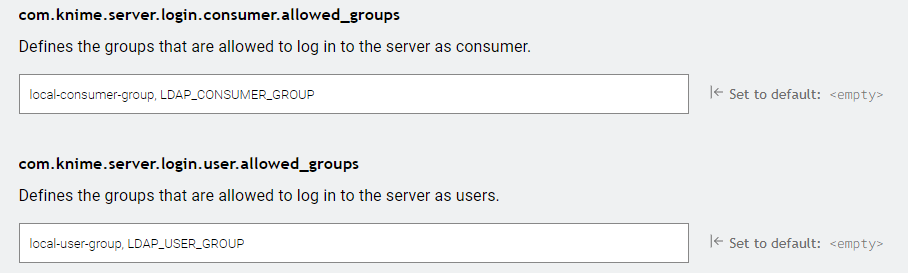
However, since we have many users, we don’t want to specify each user separately here, but - of course - we just want to use LDAP groups to specify allowed users and consumers. But for some reason, that doesn’t work:
Question: is it really correct that we can simply add the LDAP group names in these two fields together with or right next to the local group names? No need to mark them as LDAP groups?
And another question:
This regards the setting com.knime.server.login.allowed_groups
The user guide says " This setting has to include all groups that should be allowed to login to KNIME Server, regardless of whether they are users or consumers." Is that really correct? If that’s really the case, why doesn’t the KNIME server simply create this list automatically?? Why do I have to specify it manually? I mean, it’s just the UNION of the two setings user.allowed_groups and consumer.allowed_groups. Why should any user or consumer NOT be in the list of allowed login? That doesn’t really make sense. My feeling is that there is another meaning to this setting which is not mentioned in the user guide. Can someone please comment on this? Thank you!