Hi Alexander -
No problem - I appreciate you looking at this. To check I’ve executed under the right conditions, I’ll try and be pedantic in my response:
In KNIME 3.7.2:
- The NTLM (Labs) option is shown on the authentication tab of the POST request node.
- It still executes successfully, using None as the authentication option.
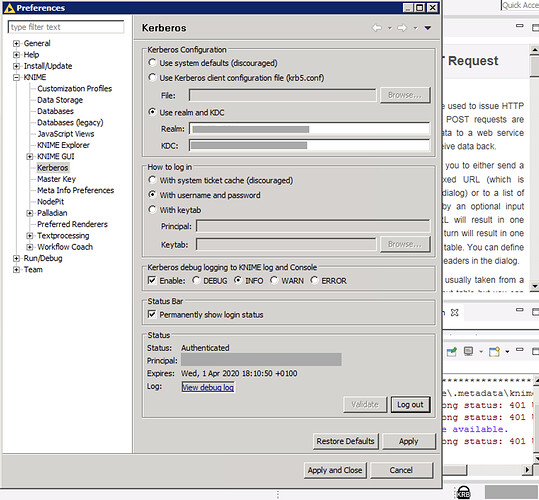
In KNIME 4.1.2:
- I clicked the Restore Defaults option on the Kerberos preferences page.
- Added
-Djava.security.krb5.debug=true to the knime.ini file.
- Restarted KNIME, using the
-consoleLog option on the command line (this was the only option I could find through searching - let me know if I need to do something else to get system out/error).
- The output is below:
During startup:
CompilerOracle: exclude javax/swing/text/GlyphView.getBreakSpot
May 07, 2020 9:54:30 AM org.apache.cxf.bus.osgi.CXFExtensionBundleListener addExtensions
INFO: Adding the extensions from bundle org.apache.cxf.cxf-rt-transports-http (135) [org.apache.cxf.transport.http.HTTPTransportFactory, org.apache.cxf.transport.http.HTTPWSDLExtensionLoader, org.apache.cxf.transport.http.policy.HTTPClientAssertionBuilder, org.apache.cxf.transport.http.policy.HTTPServerAssertionBuilder, org.apache.cxf.transport.http.policy.NoOpPolicyInterceptorProvider]
May 07, 2020 9:54:30 AM org.apache.cxf.bus.osgi.CXFExtensionBundleListener addExtensions
INFO: Adding the extensions from bundle org.apache.cxf.cxf-rt-transports-http-hc (136) [org.apache.cxf.transport.http.HTTPConduitFactory, org.apache.cxf.transport.ConduitInitiator]
!SESSION 2020-05-07 09:54:23.128 -----------------------------------------------
eclipse.buildId=unknown
java.version=1.8.0_202
java.vendor=AdoptOpenJdk
BootLoader constants: OS=win32, ARCH=x86_64, WS=win32, NL=en_US
Command-line arguments: -os win32 -ws win32 -arch x86_64 -consoleLog
!ENTRY org.eclipse.ui 2 0 2020-05-07 09:54:43.503
!MESSAGE Warnings while parsing the key bindings from the 'org.eclipse.ui.commands' and 'org.eclipse.ui.bindings' extension point
!SUBENTRY 1 org.eclipse.ui 2 0 2020-05-07 09:54:43.503
!MESSAGE Cannot bind to an undefined command: plug-in='org.knime.workbench.editor', id='knime.commands.editor.gridSettings'
!ENTRY org.eclipse.jface 2 0 2020-05-07 09:54:46.553
!MESSAGE Keybinding conflicts occurred. They may interfere with normal accelerator operation.
!SUBENTRY 1 org.eclipse.jface 2 0 2020-05-07 09:54:46.553
!MESSAGE A conflict occurred for CTRL+F:
Binding(CTRL+F,
ParameterizedCommand(Command(org.eclipse.ui.edit.findReplace,Find and Replace,
Find and replace text,
Category(org.eclipse.ui.category.edit,Edit,null,true),
org.eclipse.ui.internal.WorkbenchHandlerServiceHandler@71ee2fff,
,,true),null),
org.eclipse.ui.defaultAcceleratorConfiguration,
org.eclipse.ui.contexts.window,,,system)
Binding(CTRL+F,
ParameterizedCommand(Command(knime.commands.findnode,Find Node...,
Finds a Node in the workflow.,
Category(knime.command.category,KNIME Workflow Editor commands,Commands available for the workflow editor,true),
org.eclipse.ui.internal.WorkbenchHandlerServiceHandler@68f2363,
,,true),null),
org.eclipse.ui.defaultAcceleratorConfiguration,
org.eclipse.ui.contexts.window,,,system)
!ENTRY org.eclipse.equinox.p2.core 4 0 2020-05-07 09:54:48.599
!MESSAGE Exception during event notification
!STACK 0
java.lang.IllegalArgumentException: Location must be absolute: ..
at org.eclipse.equinox.internal.p2.repository.helpers.AbstractRepositoryManager.checkValidLocation(AbstractRepositoryManager.java:749)
at org.eclipse.equinox.internal.p2.repository.helpers.AbstractRepositoryManager.contains(AbstractRepositoryManager.java:253)
at org.eclipse.equinox.internal.p2.repository.helpers.AbstractRepositoryManager.addRepository(AbstractRepositoryManager.java:166)
at org.eclipse.equinox.internal.p2.repository.helpers.AbstractRepositoryManager.notify(AbstractRepositoryManager.java:820)
at org.eclipse.equinox.internal.p2.core.ProvisioningEventBus.dispatchEvent(ProvisioningEventBus.java:108)
at org.eclipse.equinox.internal.p2.core.ProvisioningEventBus.dispatchEvent(ProvisioningEventBus.java:1)
at org.eclipse.osgi.framework.eventmgr.EventManager.dispatchEvent(EventManager.java:230)
at org.eclipse.osgi.framework.eventmgr.EventManager$EventThread.run(EventManager.java:340)
!ENTRY org.eclipse.equinox.p2.core 4 0 2020-05-07 09:54:48.631
!MESSAGE Exception during event notification
!STACK 0
java.lang.IllegalArgumentException: Location must be absolute: ..
at org.eclipse.equinox.internal.p2.repository.helpers.AbstractRepositoryManager.checkValidLocation(AbstractRepositoryManager.java:749)
at org.eclipse.equinox.internal.p2.repository.helpers.AbstractRepositoryManager.contains(AbstractRepositoryManager.java:253)
at org.eclipse.equinox.internal.p2.repository.helpers.AbstractRepositoryManager.addRepository(AbstractRepositoryManager.java:166)
at org.eclipse.equinox.internal.p2.repository.helpers.AbstractRepositoryManager.notify(AbstractRepositoryManager.java:820)
at org.eclipse.equinox.internal.p2.core.ProvisioningEventBus.dispatchEvent(ProvisioningEventBus.java:108)
at org.eclipse.equinox.internal.p2.core.ProvisioningEventBus.dispatchEvent(ProvisioningEventBus.java:1)
at org.eclipse.osgi.framework.eventmgr.EventManager.dispatchEvent(EventManager.java:230)
at org.eclipse.osgi.framework.eventmgr.EventManager$EventThread.run(EventManager.java:340)
When executing the node:
ERROR KNIME-Worker-4-POST Request 0:1 Node Execute failed: Wrong status: 401 Unauthorized
java.lang.IllegalStateException: Wrong status: 401 Unauthorized
at org.knime.rest.nodes.common.RestNodeModel.checkResponse(RestNodeModel.java:793)
at org.knime.rest.nodes.common.RestNodeModel.makeFirstCall(RestNodeModel.java:406)
at org.knime.rest.nodes.common.RestNodeModel.execute(RestNodeModel.java:340)
at org.knime.core.node.NodeModel.execute(NodeModel.java:737)
at org.knime.core.node.NodeModel.executeModel(NodeModel.java:571)
at org.knime.core.node.Node.invokeFullyNodeModelExecute(Node.java:1236)
at org.knime.core.node.Node.execute(Node.java:1016)
at org.knime.core.node.workflow.NativeNodeContainer.performExecuteNode(NativeNodeContainer.java:557)
at org.knime.core.node.exec.LocalNodeExecutionJob.mainExecute(LocalNodeExecutionJob.java:95)
at org.knime.core.node.workflow.NodeExecutionJob.internalRun(NodeExecutionJob.java:218)
at org.knime.core.node.workflow.NodeExecutionJob.run(NodeExecutionJob.java:124)
at org.knime.core.util.ThreadUtils$RunnableWithContextImpl.runWithContext(ThreadUtils.java:334)
at org.knime.core.util.ThreadUtils$RunnableWithContext.run(ThreadUtils.java:210)
at java.util.concurrent.Executors$RunnableAdapter.call(Executors.java:511)
at java.util.concurrent.FutureTask.run(FutureTask.java:266)
at org.knime.core.util.ThreadPool$MyFuture.run(ThreadPool.java:123)
at org.knime.core.util.ThreadPool$Worker.run(ThreadPool.java:246)
Trying the Erlwood extension:
- Installed the latest version of the two community Erlwood extensions.
- Restarted KNIME.
- Changed the POST request node to use the new NTLM authentication option.
- Executed the node.
- Received a 401 error.
- In the console log, the error shown was the same - identical stack trace, with the only difference being a slightly different first line:
ERROR KNIME-Worker-4-POST Request 2:1 Node Execute failed: Wrong status: 401 Unauthorized
If there’s anything I’ve missed on here, or more details that would help - please let me know.
Thanks,
Graham