I have some good news and possibly some bad news depending on how much support you can get from your Snowflake support team, and how much you are able to do yourself!
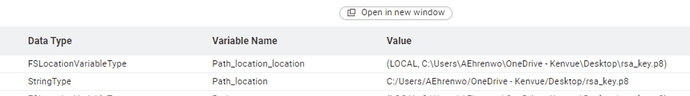
First piece of good news is that I found when I tried it that the direction of the slashes doesn’t matter 
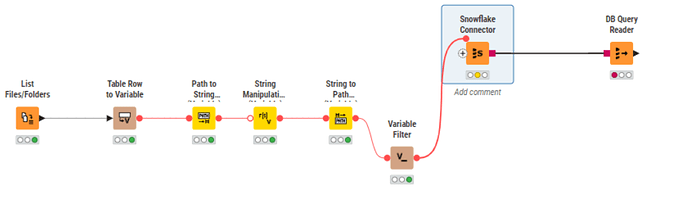
The second piece of good news is that after much trial and error and long conversations with chatGPT, I managed to connect KNIME (5.4) to snowflake with public/private key.
The bad news is that I only managed to do it if the private key file is not encrypted. And if your support team followed the Snowflake documentation, they encrypted it, hence you have a password to put in the private_key_file_pwd.
Good news again - it is possible to create a decrypted version of the private key file without changing the public key!
Do you have openssl available? If so, in a command prompt, enter the following:
openssl rsa -in rsa_key.p8 -out rsa_key_unencrypted.p8
You’ll need to run this in the folder containing your rsa_key.p8 file, and enter the password for the .p8 file when prompted
(replace rsa_key.p8 and rsa_key_unencrypted.p8 with your original p8 filename and an output filename of your choosing, having first made sure you have a backup of the rsa_key.p8 file  )
)
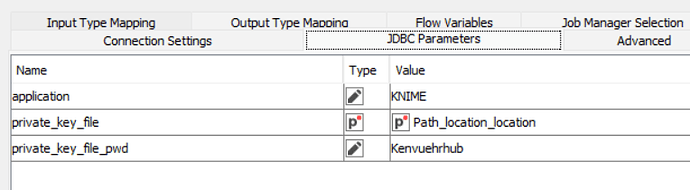
Once you have that, in your snowflake config, set private_key_file to your new filename, and completely remove (or rename) the “private_key_file_pwd” key from JDBC parameters. If the private_key_file_pwd setting is there, it will still try to decrypt.
btw, you can check if a .p8 file is actually encrypted by using the following command:
openssl rsa -in rsa_key.p8 -check
If it prompts for password it is encrypted. If it doesn’t, and it displays the file contents, then it isn’t encrypted.
Let me know how you get on. If you get further errors, I’ll see if I can figure it out. Meanwhile perhaps a KNIME team member can determine if encrypted private keys are possible with KNIME.