Hi Mareike,
thanks for your response.
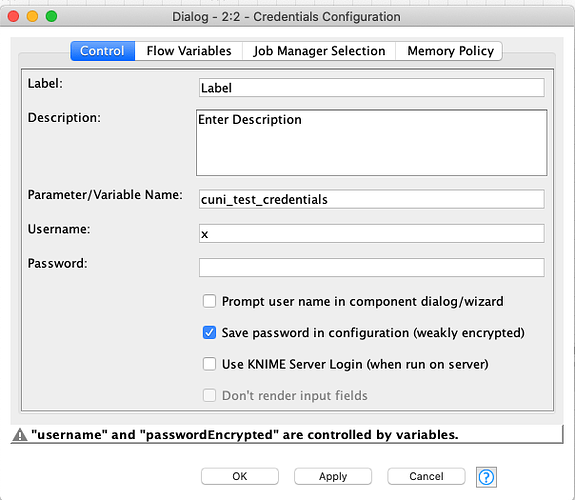
As I’ve already stated in this topic and in the topic I referred, I use in my solution property files for storing my connection params. As you can see in screenshots I provided here there is a component called DB Connection Parameters Provider which is responsible for loading connection parameters for a particular database I want to communicate with. The subsequent Credentials Configuration node is configured with the parameters the component provides as flow variables. Which is a problem when I switch the “Save password in configuration (Weakly encrypted)” option as you recommend. If I do that, my solution just stops working and I face an error my DB Connector produces: “Execute failed: ORA-01005”, which means that no password was provided. Well, if I have a closer look at Credentials Configuration node’s configuration I can see the option mentioned above has a side effect when switched. This is how the Flow Variables tab of the configuration dialog looks like when the option is not checked:
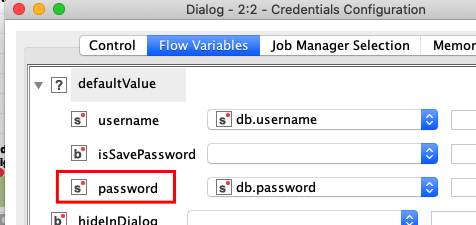
And this is how it changes after the option gets checked:
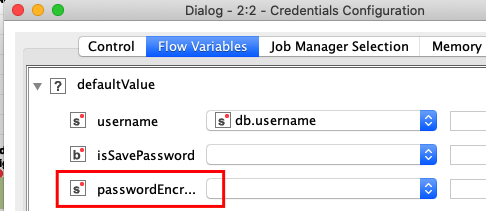
You can see, the password parameter has changed its name to “passwordEncr…” (I usually don’t see whole parameter name if it gets longer on my mac) and it has cleared. Now I bind my workflow variable again (ignoring the password in the flow variable is not encrypted):
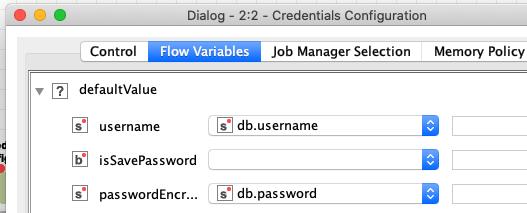
If I execute the Credentials Configuration and the subsequent PostgreSQLConnector after that, I get the same error as if I didn’t bind the variable at all. So I have a suspicion that if I check the “save password” option the node starts ignoring the fact the parameter is configured by a workflow variable even though it claims it is aware of it.
I have to complain since I started using Credentials Configuration node at the end of 2019 I keep solving problems related to it which is the reason I opened my DB Connector - Give the password flow variable configuration option back. - #3 by jan_lender topic. And I’m pretty sure things would get easier for me if I really have the option of getting rid of the need of Credentials Configuration node.
You mentioned security is the reason you as KNIME team discourage users from saving passwords to configuration. I’d bet this could have been the reason you originally introduced the credentials-over-plain-password concept. I’d like to let you know, KNIME users can keep their passwords safe even without your effort. In my case, we plan running KNIME workflows in batch mode on Linux machines. We don’t expect unauthorized persons having access to these machines so we don’t concern about plain passwords stored on their file systems.